- In env file change GATEWAY, SUBNET, and IP variables for the various networks and containers, API, APP, and MESH URL variables to suit environment. Edit remaining env to suit your config.
If running HAProxy on same system as docker containers, set http and https exp port variables to 127.0.1.1:port
Keep NATS exp port variable as 4222 and ensure firewall access. This requires a TCP only reverse proxy, and is not http traffic, so it cannot be routed through a proxy on port 443 along with the rest.
If running IPTables firewall in Drop All by default with HAProxy on the same system, make sure to add the following:
# This ensures communication because HAProxy and Docker don't play nice with Drop all by default
-A INPUT -i trmmproxy -p tcp -m multiport --sports 4443,8080 -m conntrack --ctstate NEW,ESTABLISHED -j ACCEPT
-A INPUT -i trmmproxy -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT
-A OUTPUT -o trmmproxy -m conntrack --ctstate NEW,ESTABLISHED,RELATED -j ACCEPT
-A OUTPUT -o trmmnats -m conntrack --ctstate NEW,ESTABLISHED,RELATED -j ACCEPT
- Add RMM, API, and Mesh sites to /etc/hosts
127.0.1.1 api-tactical.example.com api-tactical
127.0.1.1 rmm-tactical.example.com rmm-tactical
127.0.1.1 mesh-tactical.example.com mesh-tactical
-
Bring up stack once, then immediately stop the stack.
-
Copy valid fullchain cert and private key to "/path/to/docker/volumes/name_of_stack_data/_data/certs/" as fullchain.pem and privkey.pem respectively.
-
Start stack, verify access after init complete.
-
Log into mesh.example.com and configure 2fa, as well as client remote access settings for notification, permission, etc.
Requires HAProxy 2.4+
Make sure firewall rules are in place, then edit HAProxy config.
Assumes existing shared http to https redirect and https frontends. See full HAProxy config example in HAProxy-Example.cfg if starting from scratch for reference to configure global, default, and shared http redirect and https front ends before continuing.
Example for T-RMM, edit urls and ports to suit environment:
If not already present, add to both http and https shared frontends
option forwardfor
http-request add-header X-Real-IP %[src]
Add http to https redirects for Mesh, RMM, and API in shared http frontend
acl rmm var(txn.txnhost) -m str -i rmm-tactical.example.com
acl api var(txn.txnhost) -m str -i api-tactical.example.com
acl mesh var(txn.txnhost) -m str -i mesh-tactical.example.com
http-request redirect scheme https if rmm
http-request redirect scheme https if api
http-request redirect scheme https if mesh
Add https frontend Mesh, RMM, and API entries
acl rmm var(txn.txnhost) -m str -i rmm-tactical.example.com
acl api var(txn.txnhost) -m str -i api-tactical.example.com
acl is_websocket hdr(Upgrade) -i WebSocket
acl mesh var(txn.txnhost) -m str -i mesh-tactical.example.com
use_backend rmm-tactical.example.com_ipvANY if rmm
use_backend rmm-tactical.example.com_ipvANY if api
use_backend mesh-tactical.example.com-websocket_ipvANY if is_websocket mesh
use_backend mesh-tactical.example.com_ipvANY if mesh
Add backends
backend rmm-tactical.example.com_ipvANY
mode http
log global
timeout connect 30000
timeout server 30000
retries 3
http-request add-header X-Forwarded-Host %[req.hdr(Host)]
http-request add-header X-Forwarded-Proto https
server rmm 127.0.1.1:4443 ssl verify none
backend mesh-tactical.example.com-websocket_ipvANY
mode http
log global
timeout connect 3000
timeout server 3000
retries 3
timeout tunnel 3600000
http-request add-header X-Forwarded-Host %[req.hdr(Host)]
http-request add-header X-Forwarded-Proto https
server mesh-websocket 127.0.1.1:4443 ssl verify none
backend mesh-tactical.example.com_ipvANY
mode http
log global
timeout connect 15000
timeout server 15000
retries 3
timeout tunnel 15000
http-request add-header X-Forwarded-Host %[req.hdr(Host)]
http-request add-header X-Forwarded-Proto https
server mesh 127.0.1.1:4443 ssl verify none
Restart HAProxy service.
Test access to rmm-tactical.example.com and mesh-tactical.example.com
Go to System > Package Manager
Select Available Packages
Find and install haproxy-devel
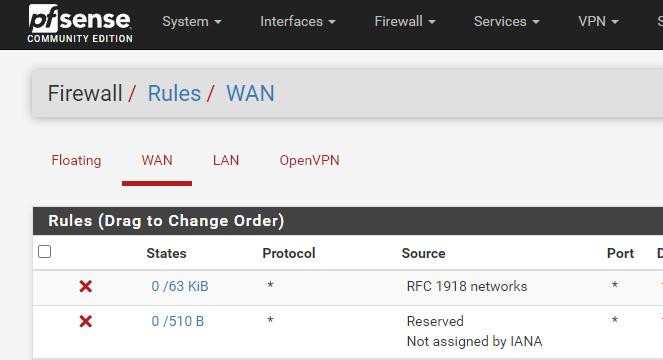
Go to Firewall > Rules
Select the WAN tab
Add the HAProxy_HTTP rule to the bottom of the list. Nothing else should have ports 80 or 443 in use.
HTTP rule:
Action = Pass
Interface = WAN
Address Family = IPv4
Source = any
Destination = This firewall (self)
Destination Port Range = From: HTTP (80), To: HTTP (80)
Log = Log packets optional
Description = HAProxy_HTTP
Save the new rule and apply changes
Copy the HTTP rule, changing the To and From ports to HTTPS (443) and the description to HAProxy_HTTPS
Save the new rule and apply changes
Go to Services > HAProxy
Select the Settings tab
Fill in the entries as shown in the screen capture below, leaving the rest at defaults or tune them to your preference:
Enable HAProxy = Checked
Reload behavior = Checked (closes existing connections to force reconnect to updated process after haproxy restart)
SSL/TLS Compatibility Mode = Intermediate (allows for maximum compatibility with all devices, select Modern at your own risk)
Max SSL Diffie-Hellman size = 2048 or 4096 (dealers choice)
Save settings and apply changes
Go to the Frontend tab. Click the button to add a new frontend.
This shared http frontend will redirect all configured entries to their HTTPS equivalent and allow SSL offloading, as well as both internal and external access to the sites/services via URL.
Fill in the entries as shown in the screen captures below:
Name = http_shared
Description = http_shared
Status = Active
External address = Listen address: any (IPv4), Port: 80
Type = http / https(offloading)
Edit entries to suit your URLs
Access Control lists:
First ACL = Name: rmm , Expression: Host matches , Value: rmm.example.com
Second ACL = Name: api , Expression: Host matches , Value: api.example.com
Third ACL = Name: mesh , Expression: Host matches , Value: mesh.example.com
Actions:
First action = Action: http-request redirect , Condition acl names: rmm , rule: scheme https
Second action = Action: http-request redirect , Condition acl names: api , rule: scheme https
Third action = Action: http-request redirect , Condition acl names: mesh , rule: scheme https
Default Backend: None
Advanced Settings:
Use "forwardfor" option = checked
Use "httpclose" option = http-server-close
Advanced pass thru =
http-request add-header X-Real-IP %[src]
Save and apply changes.
Copy the http to https redirect frontend, and edit it to match the settings below. Remove unnecessary settings.
Fill in the entries as shown in the screen captures below:
Name = https_shared
Description = https_shared
Status = Active
External address = Listen address: any (IPv4) , Port: 443 , SSL Offloading: checked
Type = http / https(offloading)
Advanced Settings:
Use "forwardfor" option = checked
Use "httpclose" option = http-server-close
Advanced pass thru =
http-request add-header X-Real-IP %[src]
SSL Offloading
Certificate = configured LetsEncrypt Server cert , Add ACL for certificate Subject Alternative Names : checked
OCSP = checked
Save and apply changes.
Go to the Backend tab and add a new backend.
Fill in the entries as shown in the screen captures below, changing entries to suit environment. Assumes port 4443 exposed on T-RMM proxy:
Name = mesh.example.com
Server list = Mode: active , Name: mesh , Forwardto: Address+Port , Address: host server IP , Port: 4443 , Encrypt(SSL): yes/checked , SSL checks: no/unchecked
Connection timeout = 15000
Server timeout = 15000
Retries = 3
Health check method = none
Advanced settings
Backend pass thru =
timeout tunnel 15000
http-request add-header X-Forwarded-Host %[req.hdr(Host)]
http-request add-header X-Forwarded-Proto https
Save and apply changes.
Copy the mesh backend and edit it
Fill in the entries as shown in the screen captures below, changing entries to suit environment:
Name = mesh.example.com-websocket
Server list = Mode: active , Name: mesh-websocket , Forwardto: Address+Port , Address: host server IP , Port: 4443 , Encrypt(SSL): yes/checked , SSL checks: no/unchecked
Connection timeout = 3000
Server timeout = 3000
Retries = 3
Health check method = none
Advanced settings
Backend pass thru =
timeout tunnel 3600000
http-request add-header X-Forwarded-Host %[req.hdr(Host)]
http-request add-header X-Forwarded-Proto https
Save and apply changes.
Copy the mesh backend and edit it
Fill in the entries as shown in the screen captures below, changing entries to suit environment:
Name = rmm.example.com
Server list = Mode: active , Name: rmm , Forwardto: Address+Port , Address: host server IP , Port: 4443 , Encrypt(SSL): yes/checked , SSL checks: no/unchecked
Connection timeout = 30000
Server timeout = 30000
Retries = 3
Health check method = none
Advanced settings
Backend pass thru =
http-request add-header X-Forwarded-Host %[req.hdr(Host)]
http-request add-header X-Forwarded-Proto https
Save and apply changes.
Go to the Frontend tab and add a new frontend
Fill in the entries as shown in the screen captures below:
Name = rmm
Description = rmm.example.com
Status = Active
Shared Frontend = checked
Primary frontend = https_shared - http
Access Control lists:
First ACL = Name: rmm , Expression: Host matches , Value: rmm.example.com
Second ACL = Name: api , Expression: Host matches , Value: api.example.com
Third ACL = Name: is_websocket , Expression: Custom acl , Value: hdr(Upgrade) -i WebSocket
Fourth ACL = Name: mesh , Expression: Host matches , Value: mesh.example.com
Actions:
First action = Action: Use Backend , Condition acl names: rmm , backend: rmm.example.com
Second action = Action: Use Backend , Condition acl names: api , backend: rmm.example.com
Third action = Action: Use Backend , Condition acl names: is_websocket mesh , backend: mesh.example.com-websocket
Fourth action = Action: Use Backend , Condition acl names: mesh , backend: mesh.example.com
Default Backend: None
Save and apply changes.
Test access to rmm.example.com and mesh.example.com